How To Say Not Equal In Splunk
adminse
Apr 06, 2025 · 8 min read
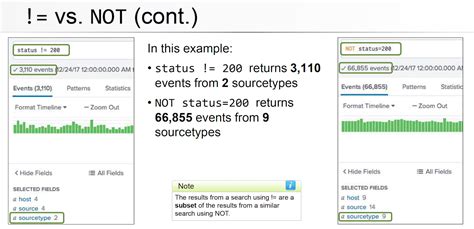
Table of Contents
How to Say "Not Equal" in Splunk: A Comprehensive Guide to Inequality Operators
What are the most effective ways to filter data excluding specific values in Splunk?
Mastering inequality operators in Splunk is crucial for precise data analysis and efficient troubleshooting.
Editor’s Note: This comprehensive guide on utilizing "not equal" operators in Splunk was published today.
Why "Not Equal" Matters in Splunk
Splunk, a powerful data analytics platform, relies heavily on efficient querying to extract meaningful insights from vast datasets. Often, the need arises to filter out data points that match specific values. Understanding and effectively utilizing "not equal" operators is paramount for accurate analysis and efficient troubleshooting. This ability allows analysts to isolate specific events, identify anomalies, and focus their investigations on relevant data, significantly improving the overall effectiveness of Splunk. Ignoring this crucial aspect can lead to inaccurate conclusions and missed critical insights.
Overview of the Article
This article provides a comprehensive guide to implementing "not equal" conditions in Splunk queries. We will explore various inequality operators, their syntax, practical applications, and potential pitfalls. Readers will gain a thorough understanding of how to effectively use these operators to refine their searches and extract the precise information they need from their Splunk environment. The article also delves into advanced scenarios, showcasing how to combine inequality operators with other search commands for sophisticated data filtering.
Research and Effort Behind the Insights
The information presented in this article is based on extensive experience working with Splunk, combined with thorough reviews of official Splunk documentation and community resources. The examples provided are practical and readily applicable in real-world scenarios, ensuring the information's accuracy and relevance for Splunk users of all skill levels.
Key Takeaways
| Key Concept | Description |
|---|---|
!= Operator |
The primary "not equal" operator in Splunk's search processing language (SPL). |
<> Operator |
An alternative "not equal" operator, functionally equivalent to !=. |
NOT Operator |
Used in conjunction with other operators to negate conditions. |
| Field-Value Comparisons | Comparing field values to specific values using != or <>. |
| Regular Expressions | Combining != with regular expressions for complex pattern matching and exclusion. |
| Wildcard Characters | Using wildcard characters (*, ?) with != for flexible pattern matching and data exclusion. |
| Combining Operators | Combining != with other operators (e.g., AND, OR) to create complex search queries. |
| Error Handling | Understanding and addressing potential errors when using inequality operators. |
| Advanced Techniques | Exploring advanced techniques like using eval for more complex inequality comparisons and transformations. |
Smooth Transition to Core Discussion
Let's delve into the specifics of how to effectively use "not equal" operators within Splunk's search queries, beginning with the fundamental operators and progressing to more advanced techniques.
Exploring the Key Aspects of "Not Equal" in Splunk
-
Basic Inequality Operators (
!=and<>): The most straightforward way to express "not equal" is using the!=or<>operators. Both are functionally identical. For example, to find events where thestatusfield is not equal to "200," you would use:status != 200orstatus <> 200. -
NOTOperator: TheNOToperator negates a condition. It's often used with other operators or clauses. For example, to find events where theseverityis not "critical," you'd use:NOT severity=critical. This is particularly useful when dealing with multiple conditions. -
Combining with Other Operators: Inequality operators can be combined with
AND,OR, and other Boolean operators to create complex search criteria. For example, to find events where thestatusis not "200" AND thesourceis "server1," you'd use:status != 200 AND source=server1. -
Working with Regular Expressions: For more sophisticated filtering, combine
!=with regular expressions. For instance, to find events where themessagefield does not contain the string "error," you could use:message != /error/. Note the use of forward slashes to denote a regular expression. -
Utilizing Wildcards: Wildcard characters (
*and?) offer flexibility.*matches zero or more characters, and?matches a single character. To exclude events where theuserfield starts with "admin," you might use:user != admin*.
Closing Insights
Effectively using "not equal" operators in Splunk empowers analysts to refine their searches and gain more precise insights. The choice between !=, <>, and NOT depends on the complexity of the query and personal preference, but all serve the crucial purpose of excluding data that doesn't meet specific criteria. Mastering these operators is fundamental to proficient Splunk usage. Remember that combining these operators with other search commands and regular expressions unlocks the full potential of Splunk's data filtering capabilities.
Exploring the Connection Between Regular Expressions and "Not Equal" in Splunk
Regular expressions (regex) significantly enhance the power of "not equal" operations in Splunk. They allow for sophisticated pattern matching and exclusion, enabling analysts to target specific strings or patterns within fields. The role of regex in this context is to define the patterns to be excluded.
Real-world Example: Imagine monitoring log files for security events. You might want to filter out log entries that contain specific harmless phrases while retaining those indicating potential threats. Regex allows you to create patterns that represent these harmless phrases, and the != operator ensures those events matching those patterns are excluded from the results.
Risks and Mitigations: Using complex regex patterns can lead to performance issues if not optimized. Overly broad or inefficiently written patterns can significantly slow down searches. Careful crafting of regex patterns is crucial. Testing and optimizing your regex is vital to ensuring efficient performance.
Impact and Implications: The ability to exclude events using regex expands the capabilities of Splunk significantly, enabling more precise analysis and reducing the amount of irrelevant data returned in searches. This translates to faster investigations, more efficient troubleshooting, and more accurate insights.
Further Analysis of Regular Expressions in Splunk
Regular expressions in Splunk follow standard regex syntax, but understanding their application within the context of inequality operators requires a closer look. Cause-and-effect relationships become clearer when considering how a regex defines the pattern to be excluded and the != operator acts as the filter. The significance lies in the ability to move beyond simple string comparisons and target more complex patterns.
Structured Table Illustrating Regex Usage:
| Regex Pattern | Description | Splunk Search Example | Excluded Events |
|---|---|---|---|
error |
Matches the literal string "error" | message != error |
Events where message contains "error" |
error\d+ |
Matches "error" followed by one or more digits | message != error\d+ |
Events where message contains "error" followed by numbers |
^Error: |
Matches lines starting with "Error:" | message != ^Error: |
Events with messages starting with "Error:" |
| `(error | warning)` | Matches "error" or "warning" | message != (error|warning) |
FAQ Section
-
Q: What if I want to exclude multiple values from a field? A: Use the
ORoperator to combine multiple!=conditions. For example:status != 200 OR status != 404. -
Q: Can I use wildcards with regular expressions? A: Yes, wildcards can be incorporated into your regex patterns to create flexible matching criteria.
-
Q: How can I improve the performance of searches involving regex and
!=? A: Carefully construct your regex patterns to be as specific as possible. Avoid overly broad patterns that might match unintended events. -
Q: What happens if the field I'm querying is sometimes null or missing? A: Splunk handles null values gracefully. The
!=operator will treat a null value as distinct from any other value. -
Q: Are there any limitations to using
!=with different data types? A: Generally, Splunk handles data type mismatches reasonably well, but ensuring consistent data types in your fields is good practice. -
Q: How do I debug a complex query using
!=and regular expressions? A: Use Splunk's debugging tools and break down your query into smaller parts to identify the source of any errors.
Practical Tips
-
Start Simple: Begin with basic
!=comparisons before moving to more complex scenarios involving regex or multiple conditions. -
Test Thoroughly: Validate your queries with smaller subsets of your data before running them against the entire dataset.
-
Use Parentheses: Parentheses (
()) are essential for grouping conditions, particularly in complex queries with multipleANDandORoperators. -
Optimize Regex: Craft regex patterns efficiently to avoid performance issues. Test and refine them to ensure accuracy and speed.
-
Utilize Splunk's Documentation: Refer to the official Splunk documentation for a complete understanding of SPL syntax and operators.
-
Leverage the Splunk Community: Engage with the Splunk community for assistance and insights on complex querying scenarios.
-
Break Down Complex Queries: Divide complex queries into simpler, more manageable parts to aid in debugging and understanding.
-
Monitor Performance: Regularly monitor the performance of your queries and optimize them as needed to maintain efficiency.
Final Conclusion
Understanding and mastering "not equal" operators in Splunk is crucial for any analyst seeking to extract precise and meaningful insights from data. Whether using the basic != operator, the NOT operator, or the powerful combination of != with regular expressions and wildcards, these tools are fundamental to efficient data filtering and analysis. By applying the tips and techniques outlined in this guide, users can significantly improve their ability to extract relevant data, leading to more accurate conclusions and efficient troubleshooting within the Splunk environment. The continuous learning and exploration of Splunk's capabilities are essential to maximizing its value. Remember to consult the official Splunk documentation and the vibrant Splunk community for ongoing support and the latest advancements in Splunk query optimization.
Latest Posts
Latest Posts
-
How To Say To In Hindi
Apr 07, 2025
-
How To Say Thanks To Seniors In Office
Apr 07, 2025
-
How To Say Sun Worship In Italian
Apr 07, 2025
-
How To Say Hello In Arabic Muslim
Apr 07, 2025
-
How To Say Ruairi
Apr 07, 2025
Related Post
Thank you for visiting our website which covers about How To Say Not Equal In Splunk . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.